Dec 22
Allow local LAN in UFW
Quite often I have scoured the web on how to allow the "local" or "private" IP range behind my router, this 192.168... subnet, to enable one machine to access another machine on my local LAN, or in other words allow clients to connect to one another within my private LAN network, and keep everyone else blocked. And very often nothing came up, as I was not using the right keywords. So for me, and everyone else looking up "allow local ip range in ufw", here is the note on how to do that:
The idea is using a netmask, instead of adding one UFW rule for every client within the network. You might think of it as the equivalent of 192.168.1.* with the asterisk as sort-of wildcard operator, but using a wildcard is not a proper notation!
There's more on using a netmask here.
And some IP calculator showing you what it does. The screenshot is from http://www.subnet-calculator.com/cidr.php
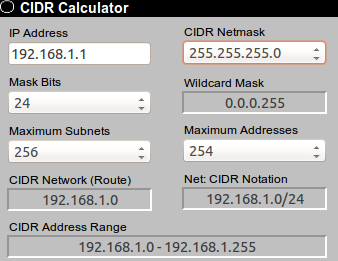
So in UFW, which is your Ubuntu front-end to iptables, you'd enter "allow IN from 192.168.1.1/24", "to 192.168.1.12" - for example, if you have a local webserver running on 192.168.1.12, or similar. You can also narrow that further down, only allowing connections IN to port 3000 or something like that. Having 192.168.1 with .1/24 means the first three numbers (octets) are fixed, only allowing the last one, here 1-255, to vary, giving every member of this subnet, or from that IP range, access to your machine 192.168.1.12. Of course, you can apply these rules for slightly different IPs within the private realm, for example many routers are configured to operate on 192.168.0.1, where the "wildcard" notation would be 192.168.0.0/24 or 192.168.0.1/24.
You could also allow the whole private network address range (192.168.0.0 to 192.168.255.255) with a lower "mask bits"-number of 16, like this 192.168.0.0/16 in CIDR notation.
For further reading, check this very good page (section "Private Addresses", nearly at the bottom) and the related RFC1918.
Keep in mind, this only works for IPv4 - with IPv6 this is a completely different story and not possible.
